Written by Petr Gotthard on Wednesday 15 December 2021 in the category Default.
Chen Zhaojun of Alibaba recently discovered a critical vulnerability in Apache Log4j that could allow an unauthenticated, remote attacker to execute arbitrary code.
Our products are not affected by this. The ICR routers, R-SeeNet, WA/VPN and WA/DMP Gen2 do not include the Log4j utility and thus are not vulnerable. Should you have more questions, please contact your Regional Support.
Written by Miloslav Bien on Thursday 6 May 2021 in the category Default.
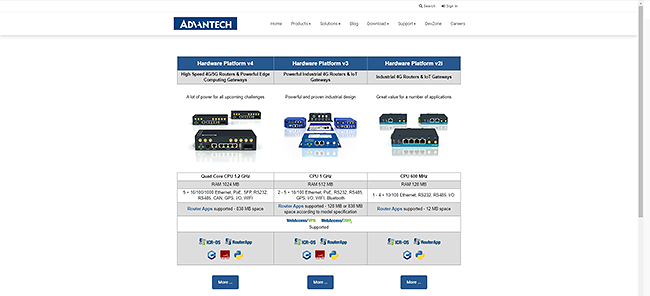
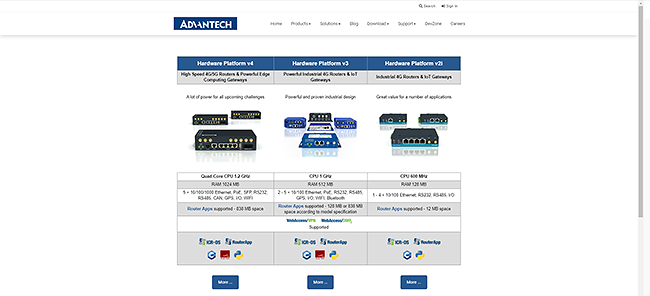
Based on the frequent requirement to clarify the differences among router hardware platforms we decided to release a comprehensive platform overview on the separate web page. With the simple matrix on platform page is much easier to understand and choose the right family of routers from HW and SW points of view.
Written by Miloslav Bien on Saturday 20 February 2021 in the category Default.

From the beginning of 2021, we started to use the new name ICR-OS (Industrial Cellular Routers OS) instead of Conel OS for the router operating system. Now we finished that transition and prepared a basic overview of ICR-OS features on the web page.
Written by Petr Gotthard on Monday 4 January 2021 in the category Default.
Forescout Research Labs has recently published a report from a study called AMNESIA:33, which performed a security analysis of seven open-source embedded TCP/IP stacks. The study discovered 33 new vulnerabilities in four of the seven analyzed stacks. For more details see the White Paper.
Our routers use the Linux Kernel TCP/IP stack, which is not affected by the listed vulnerabilities. Should you have more questions, please contact your Regional Support.
Written by Petr Gotthard on Friday 17 July 2020 in the category Default.
We released a user module with NetFlow/IPFIX probe and collector. The module captures a source and a destination IP address of each observed network communication and the amount of data exchanged. This can be used by network monitors such as PRTG to identify unusual traffic flows caused by misconfigurations, security incidents or policy violations.
Detailed description of the module configuration and operation can be found in the NetFlow/IPFIX Application Note.
The User Modules can be downloaded here.
Written by Petr Gotthard on Wednesday 24 June 2020 in the category Default.
Our cellular routers are not affected by the Ripple20 vulnerabilities discovered in a TCP/IP software library of many IoT devices.
Written by Petr Gotthard on Thursday 27 February 2020 in the category Default.
Our cellular routers are not affected by the Kr00k vulnerability because the hardware is not based on Broadcom or Cypress Wi-Fi chips.
Written by Petr Gotthard on Thursday 16 January 2020 in the category Default.
Our cellular routers are not affected by the „Cable Haunt“ vulnerability, which was recently discovered in Broadcom-based cable modems across multiple vendors.
Written by Jan Otte on Thursday 20 June 2019 in the category Default.
This security advisory is a reaction on the recently discovered network vulnerabilities in Linux kernel (see below on particular names and links).
These vulnerabilities can, under certain circumstances, be used by an attacker against a range of our routers running current firmware (6.1.9) with the potential result of the router rebooting.
We have already prepared a patch which closes the vulnerabilities. The patch will be included in future firmware versions (6.1.10, 6.2.0) when these are released.
Until the new firmware versions are available, you may apply any of the recommended workaround. The easiest ...
Written by Jan Otte on Wednesday 17 October 2018 in the category Default.

This article main topic is about v2 factory settings and default use case, also discussing a few LAN attacks on high-level.
When you get a cellular router from Advantech CZ, the default settings fall into one of the three cases:
As for the first possibility - router pre-configured exactly to your needs: as described in the first article, there are several ways how ...